Hello and welcome to CloudBreach’s first blog post on “Introduction to AWS Enumeration” with a special emphasis on the security aspects. In the dynamic realm of cloud security, the paramount first step of any offensive security engagement is undoubtedly enumeration. This methodical process of gathering comprehensive information about target systems is not just a preliminary step; it is the cornerstone upon which successful security engagements are built. Even in the intricate and expansive cloud environments, the principle of ‘Enumeration First’ holds its ground as the key to unveiling the concealed vulnerabilities and potential attack vectors.
Our short blog delves deep into unlocking the secrets of unauthenticated AWS S3 enumeration through the lens of a potential adversary. Upcoming blogposts will explore the security dimensions other AWS services.
What is Amazon S3 ?
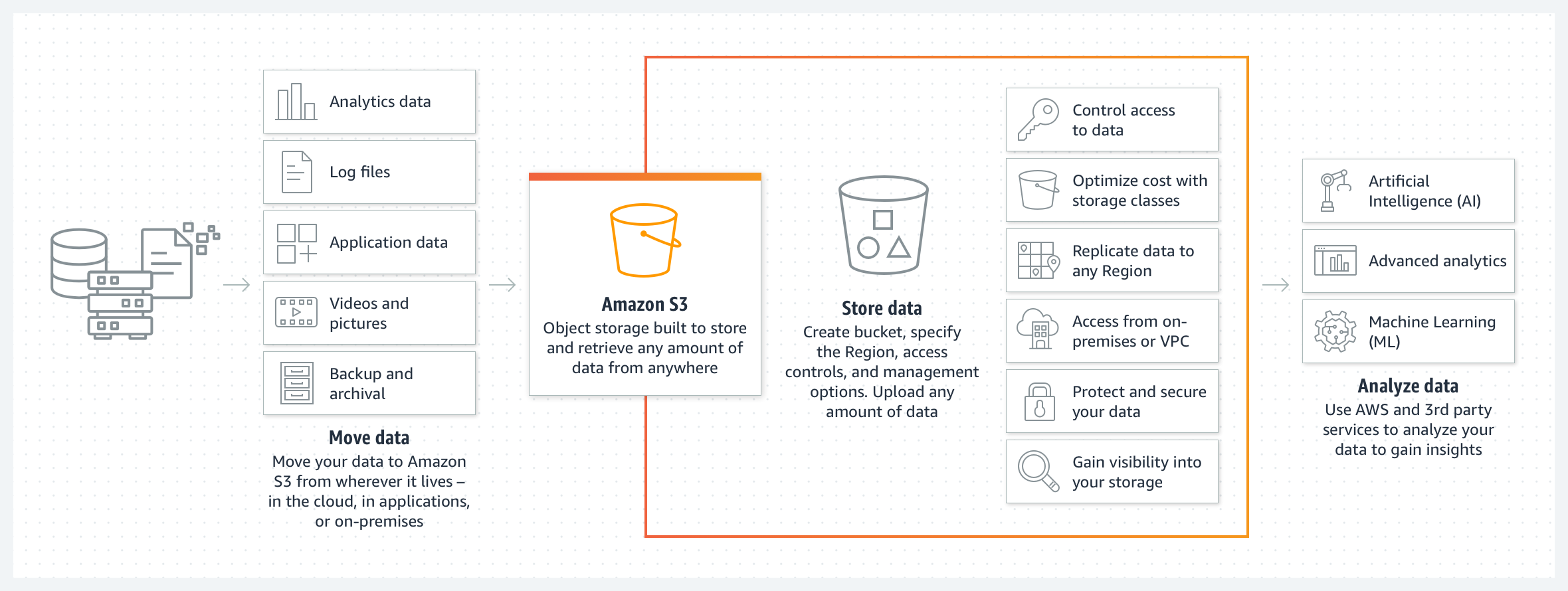
Amazon Simple Storage Service (Amazon S3) is a scalable object storage service provided by Amazon Web Services (AWS). It is designed to store and retrieve any amount of data from anywhere on the web.
Image Source: Amazon S3 Documentation [https://aws.amazon.com/s3/]
In the context of AWS enumeration, particularly when discussing Amazon S3, there are two main types of enumeration: unauthenticated and authenticated. Each type has its own methodologies, tools, limitations. In this article, we will focus on the security standpoint.
Open Source Intelligence (OSINT)
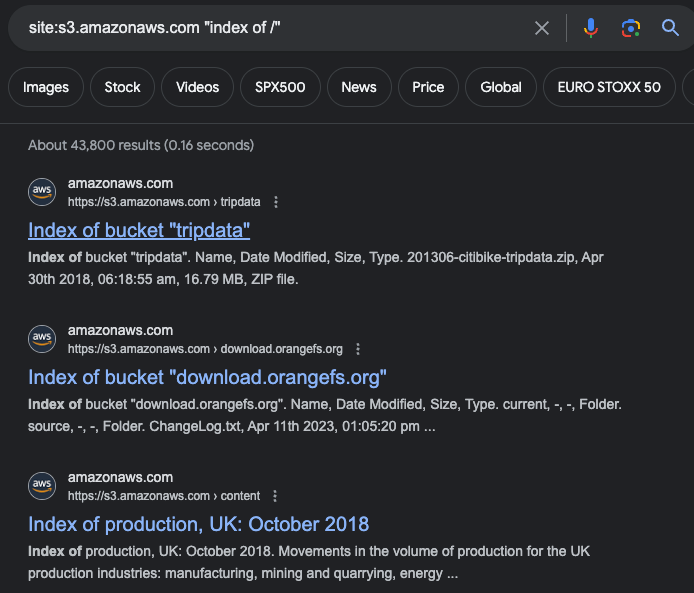
In this process we use various search engines to perform OSINT and get information about AWS Access & Secret Keys that are leaked and AWS S3 Bucket names that are cached by crawlers.
Google Dorks
The below google dorks can be used to extract the information related with AWS S3:
More Google Dorks can be found by doing a quick search on Google Hacking Database with appropriate keyword in search
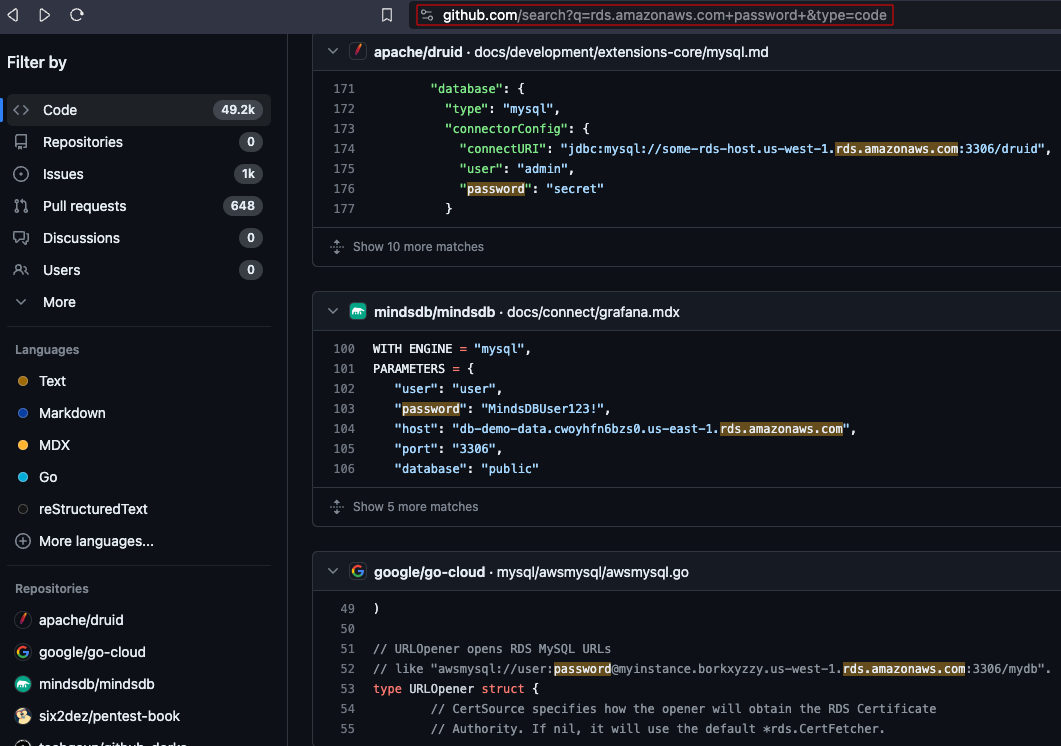
Github Dorks
These are some of the hand picked Github Dorks to enumerate AWS S3 Bucket and Secret Key and Access
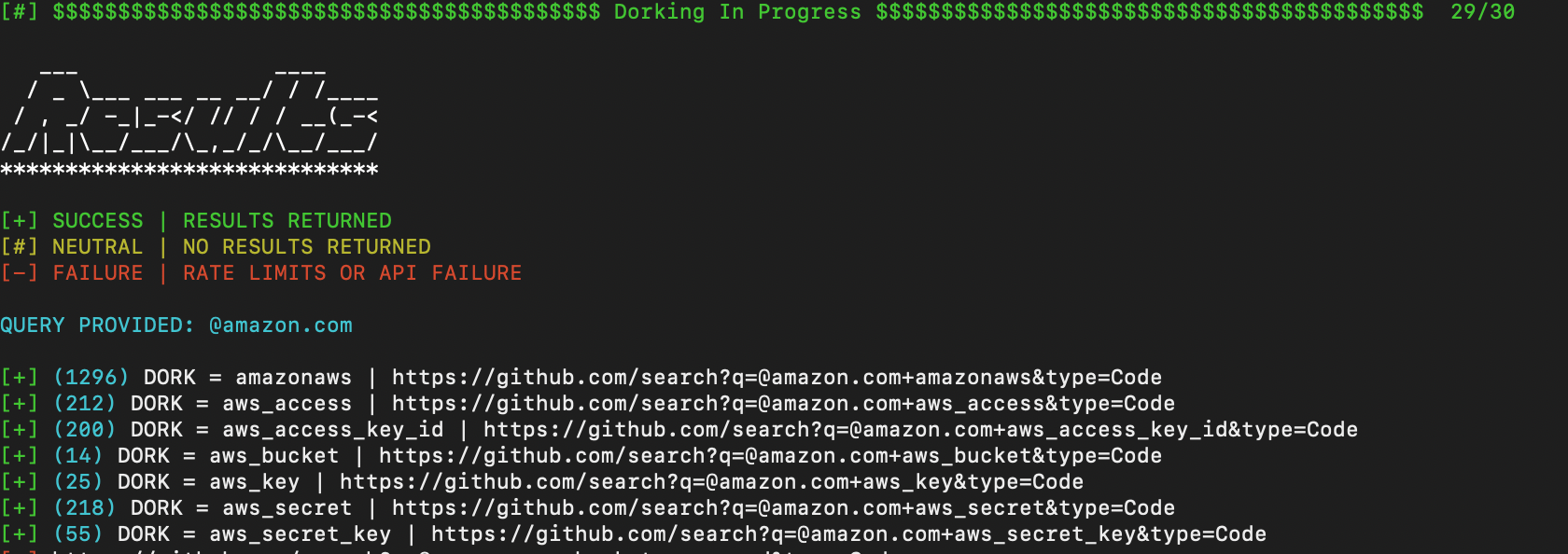
The process of searching manually for each keyword can be automated using GitDorker as shown below:
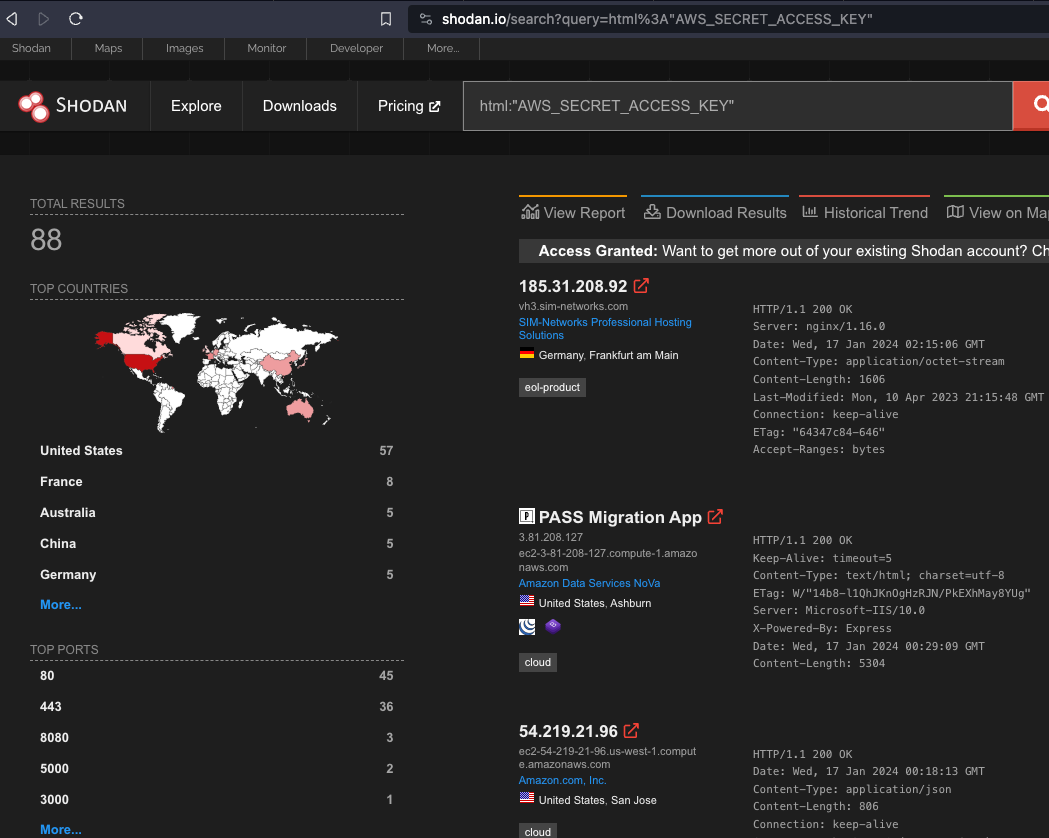
Shodan Query
According to Shodan, the data displayed are from the past 30 days of monitored data on the internet.
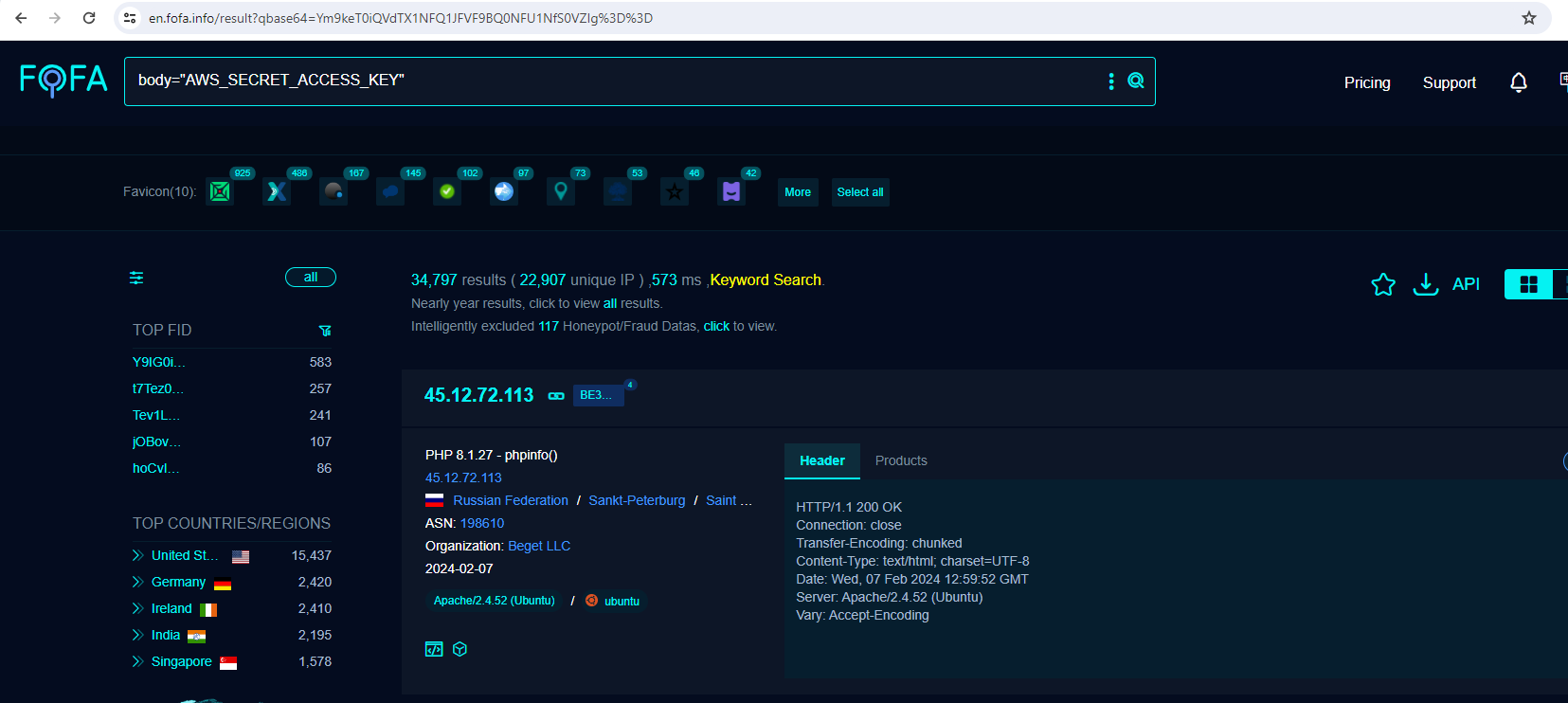
Fofa Query
FOFA is a search engine for mapping cyberspace, aimed at helping users search for internet assets on the public network.
Detecting Amazon Website using BuiltWith
BuiltWith tracks over 2500 eCommerce technologies across over 26 million eCommerce websites. You can search for other Technology of Amazon Web Services from the search tab with “Amazon” as a keyword.
Wappalyzer
Wappalyzer is a cloud technology profiler tools that analysis the technology utilised by a web application. The company has also launched a Chrome extension for more flexibility, Wappalyzer Extension.
AWS S3 Bucket Listing
S3 bucket listing refers to the ability to view and retrieve a list of files stored in an Amazon S3 bucket, providing essential insights into the contents and facilitating efficient data management. It enables users to navigate and understand the objects present within the bucket.
Using Uncover with Nuclei
- uncover – It is a go wrapper using APIs of well known search engines to quickly discover exposed hosts on the internet.
- httpx – It is a fast and multi-purpose HTTP toolkit that allows running multiple probes using the retriable http library.
- nuclei – Nuclei is a fast, template-based vulnerability scanner focused on security testing. It’s primarly used for web security testing , however it can be adapted for various types of enumeration, including AWS enumeration. It’s important to note that Nuclei is not inherently designed for cloud-specific enumerations like AWS S3 buckets.
Get all the available hosts from the internet using uncover, check if it has HTTP or HTTPS URL Schema using httpx and then scan it using the nuclei engine with aws-object-listing template. As a result, you will get the details of the Amazon(AWS) S3 buckets as shown in the below image.
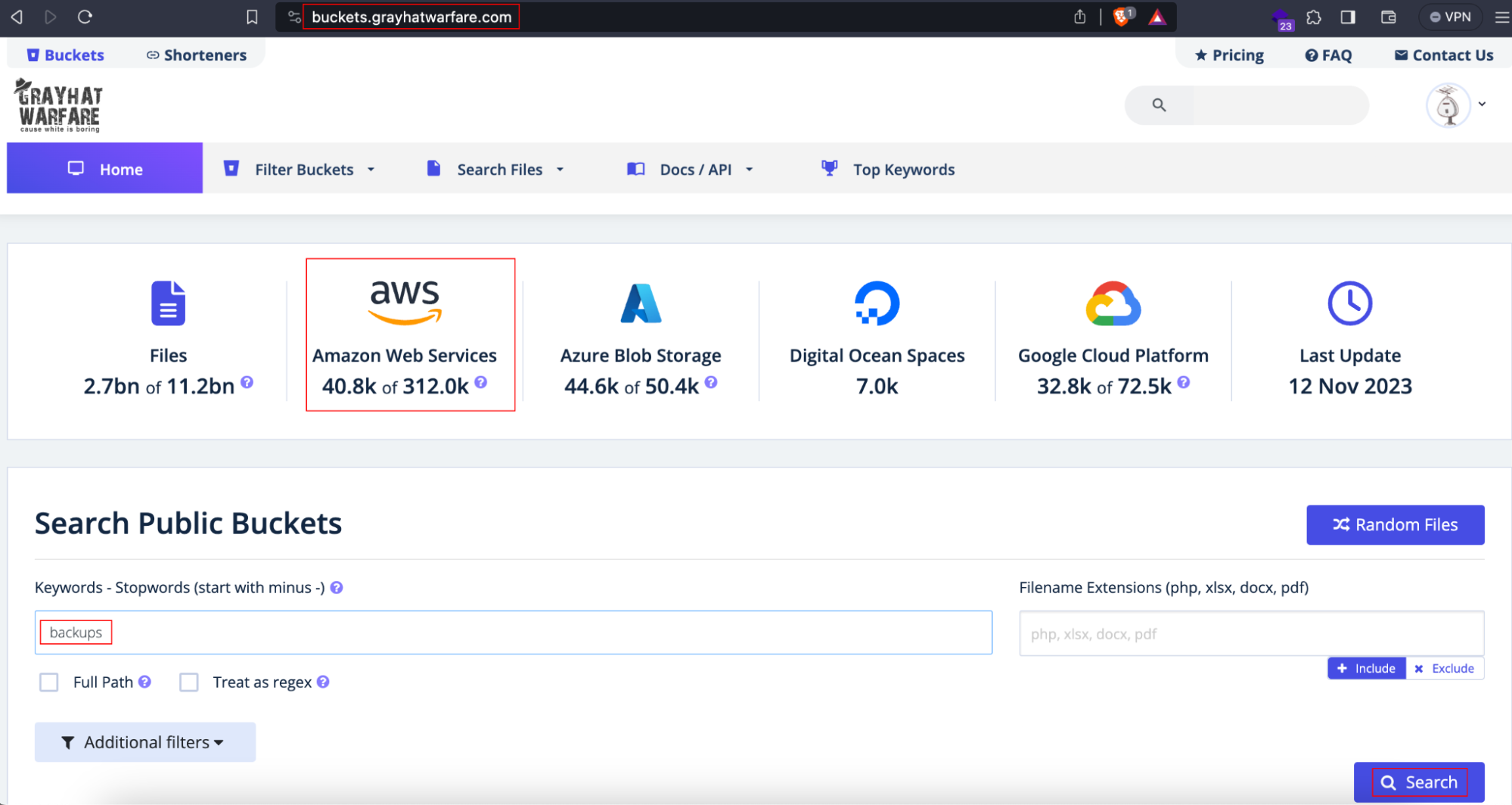
Grayhatwarfare
GrayhatWarfare allows users to find open buckets.
Conclusion
It’s crucial for individuals and organizations to prioritize the security of their AWS S3 buckets. Unauthenticated enumeration poses significant risks, potentially exposing sensitive data and leaving systems vulnerable to unauthorized access.
As we’ve explored various simple techniques and tips to map your attack surface of your organization, it’s essential to emphasize that continues testing and review of AWS services is required. Most companies, lack the cloud expertise and knowledge required to maintain cloud infrastructure making them prone to misconfigurations that can lead to data breaches.
Boost your cloud security skills and learn about the latest cloud offensive techniques by enrolling to the Breaching AWS course. The on-hangs labs provide the perfect training platform to test your tools and knowledge. Take the challenge and earn the OAWSP badge to showcase your AWS security proficiency. Stay ahead in safeguarding cloud environments against evolving threats.