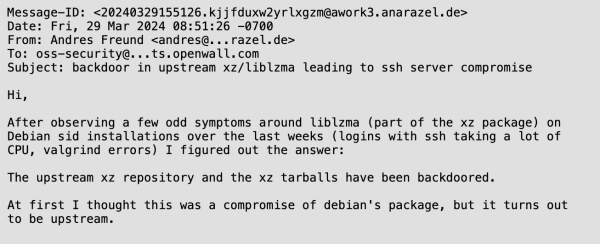
In March 2024, Microsoft employee and PostgreSQL developer Andres Freund while investigating a performance regression in Debian Sid he noticed unusually high CPU usage in SSH connections and errors in the Valgrind memory debugging tool. During his investigation, Freund discovered a backdoor in the popular Xz Utils application. He reported the findings to the Openwall Project’s security mailing list, alerting software vendors.
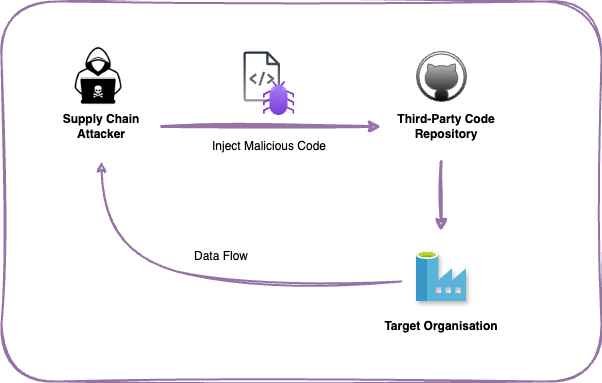
The Xz Utils backdoor supply chain attack involved the insertion of malicious code into a widely used open-source library, Xz Libs, which is essential for Unix-based systems. The attacker had attempted to obfuscate the backdoor by implementing it in multiple stages. This supply chain attack gave attackers unauthorized access and control over systems using the compromised versions of the library.
The threat was particularly severe, as it targeted a critical part of server infrastructure used by millions. This incident highlighted once more the raising trend in sophisticated supply chain attack over the recent years.
Introduction to Supply Chain Attacks
What Are Supply Chain Attacks?
Supply chain attacks have existed for decades, initially focusing on physical goods and manufacturing processes, often referred to as physical supply chain attacks. Historically, adversaries exploited networks of suppliers and manufacturing workflows to compromise the integrity of products or disrupt business operations in areas such as procurement, logistics, and production.
Over the years, as technology has advanced and software interdependencies have grown, supply chain attacks have gained significant prominence in the cybersecurity landscape. Adversaries increasingly leverage these attacks to indirectly target victims by exploiting trusted third-party vendors, tools, or services connected to their targets. The compromise of a single vendor, tool, or service can cascade across entire ecosystems, potentially impacting thousands of organizations and making this technique particularly dangerous.
Why the Cloud is a Prime Target?
It is hard to find a company that does not use cloud computing technologies today. From small startups to large enterprises, organizations across industries rely on cloud service providers (CSPs) for critical functions such as data storage, application hosting, and operational efficiency. Cloud computing has become the backbone of modern business, offering scalability, cost efficiency, and seamless integration of tools and services.
However, this reliance has also created an interconnected ecosystem that is highly attractive to adversaries. The cloud’s extensive interconnectivity, combined with third-party dependencies such as APIs, software packages, and managed services, introduces a vast and often vulnerable attack surface. This makes the cloud a prime target for attackers who seek to exploit supply chain vulnerabilities to compromise businesses indirectly.
Evolution of Supply Chain Attacks
Traditional Supply Chain Attacks
According to the blog post titled “Software Supply Chain Attacks: Insights and Defense Strategies” by Threat Intelligence Lab, modern supply chain attacks, which frequently target software development processes and tools in today’s digital age, trace their origins to traditional (physical) supply chain attacks. These earlier attacks, aimed at manufacturers, suppliers, and logistics companies, have been a persistent threat for decades. Adversaries employed various methods, such as counterfeiting, tampering with goods, theft, and causing delivery delays, to disrupt operations and introduce fraudulent products. The impact of these attacks often included delayed shipments, counterfeit goods, and substantial financial losses.
An early example of the supply chain attack technique in the digital ecosystem involved attacks on software updates and phishing attacks with malicious attachments sent to employees. According to the blog post titled “Throwback Attack: RSA SecurID Attack Shows the Importance of Protecting Critical Assets” by Control Engineering, the March 2011 cyberattack on RSA SecurID, a company that provides two-factor authentication solutions to numerous organizations, resulted in a data breach affecting 30,000 customers of its SecurID tokens. The stolen information was later used to breach RSA’s clients. Notable victims included major companies such as Lockheed Martin, a security and aerospace giant, which was forced to temporarily shut down its network and replace its SecurID tokens in response to the breach.
Modern Cloud-Centric Supply Chain Attacks
The rapid adoption of cloud computing by organizations of all sizes and individuals has made cloud platforms and services an attractive target for adversaries. Cloud-centric supply chain attacks have emerged as a significant threat, leading to widespread disruptions, data breaches, and financial losses. The challenges of managing multi-cloud and hybrid environments further exacerbates the issue, as organizations increasingly rely on multiple providers (e.g., Amazon AWS, Microsoft Azure, Google Cloud Platform) to meet their operational needs, thereby expanding the potential attack surface.
In contrast to traditional supply chain attacks that targeted physical goods or manufacturing processes (e.g., servers, networking equipment), cloud-centric supply chain attacks focus on exploiting vulnerabilities within cloud services, software dependencies, and third-party integrations. The extensive reliance on shared tools, libraries, and API services amplifies these vulnerabilities. Threat actors often remain undetected for months within compromised vendors, tools, or services, potentially impacting thousands of organizations. The consequences of these attacks range from stolen sensitive data and intellectual property to operational downtime and reputational damage, making this technique extremely dangerous.
As reported by Lucian Constantin in CSO Online on December 15, 2020, [supply chain attacks] are among the most challenging threats to mitigate. They exploit the trust established between vendors and customers, as well as automated communication channels like software update systems, which users inherently trust.
Common Cloud-Centric Supply Chain Attack Techniques
The article “The 3 Types of Cyberattacks Affecting Global Supply Chains” by Seongkyoon Jeong, published in Supply Chain Management Review, explores key cyberattack methods targeting global supply chains. Likewise, blog posts by GitGuardian and Red Canary shed light on techniques such as dependency confusion attacks and cloud API abuse, demonstrating how they can be exploited to carry out successful supply chain attacks.
- The “Fake” Supply Chain: Adversaries exploit social engineering techniques, such as phishing and impersonation, to infiltrate cloud environments. For instance, attackers may impersonate a trusted cloud service provider or supply chain partner, deceiving organizations into providing credentials or access to sensitive cloud-based systems. This method thrives in the cloud due to the heavy reliance on email and digital communication within cloud ecosystems.An example of this is when attackers, posing as a cloud storage vendor or managed service provider, send fake notifications about “account access issues,” tricking users into revealing their login credentials.
- Compromised Software Updates: Threat actors inject malicious code into software updates distributed through cloud-hosted services or applications. These updates, often trusted due to their source, are downloaded by organizations and integrated into their cloud infrastructure, unknowingly spreading malware across systems.An example is the SolarWinds attack, where attackers embedded malicious code into the Orion software updates, impacted a number of high-profile targets, including the U.S. Department of Homeland Security. The attackers were able to gain access to the networks of these organizations and potentially exfiltrate sensitive information.
- Third-Party Vendor Exploitation: Threat actors exploit vulnerabilities in third-party vendors and service providers that are critical to cloud environments. By compromising these external entities, attackers gain indirect access to the cloud systems and data of their clients. This method takes advantage of the interconnected nature of modern cloud-based supply chains, where organizations often rely on multiple external providers for essential operations.An example is the Kaseya ransomware attack that reveals a notable case of third-party vendor exploitation. The Attackers breached Kaseya, a managed service provider, and used its software update system to distribute ransomware to hundreds of downstream customers, many of whom relied on cloud-based infrastructure for their operations.
- Targeting APIs and Cloud Integrations: APIs are the backbone of cloud ecosystems, enabling integration between various services. Attackers exploit weak or misconfigured APIs to gain unauthorized access, exfiltrate data, or disrupt cloud services.An example involves attackers exploiting misconfigured AWS S3 buckets through exposed APIs has been a common tactic, leading to data leaks and security breaches.
- Dependency Confusion Attacks: This technique involves uploading malicious packages to public repositories like npm, PyPI, or RubyGems, using names that mimic legitimate internal packages. Automated CI/CD pipelines in cloud environments may unknowingly integrate these malicious packages, spreading malware.An example is the Dependency Confusion attack technique, revealed in 2021 by researcher Alex Birsan. In his article “Dependency Confusion: How I Hacked Into Apple, Microsoft and Dozens of Other Companies”, Alex unveils a novel supply chain attack method termed “dependency confusion.” This technique exploits the way software development environments handle package dependencies.Key Points from Alex supply chain attack research:
- Internal vs. Public Packages: Organizations often use private, internally developed packages alongside public packages from repositories like npm, PyPI, or RubyGems. Birsan discovered that if an internal package’s name wasn’t claimed on a public repository, the system might default to fetching the package from the public source.
- Exploitation Method: By uploading malicious packages to public repositories using the same names as unclaimed internal packages, Birsan demonstrated that systems would prioritize these public packages over the internal ones. Once integrated, these malicious packages could execute unauthorized code within the target’s environment.
- Impact: Birsan successfully tested this approach against major companies, including Apple and Microsoft, highlighting a significant vulnerability in software supply chains.
- Mitigation: To defend against such attacks, Birsan recommends measures like using scoped packages, configuring registries to prioritize internal sources, and implementing strict validation processes for dependencies.
Examples of Recent Advanced Persistent Threats (APTs) Exploiting Supply Chain Attacks
1. SolarWinds Supply Chain Attack (2021):
The SolarWinds attack, one of the most infamous supply chain breaches, targeted the Orion IT management software used by thousands of organizations worldwide. The attack began when the Russian APT group Nobelium infiltrated SolarWinds’ software development environment. The attackers injected malicious code, known as the Sunburst backdoor, into Orion’s software updates, which were distributed to SolarWinds customers through legitimate software updates to customers, which included government agencies, critical infrastructure, and private corporations.Once inside the affected environments, the attackers demonstrated advanced evasive techniques to remain undetected. They carefully selected high-value targets and used compromised credentials to pivot from on-premises systems to cloud environments. Nobelium targeted identity infrastructure, such as Microsoft Active Directory Federation Services (AD FS), to escalate privileges and gain access to cloud resources, including Microsoft 365 environments. Read More: Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor
2. PyTorch Framework Attack (2022)
In December 2022, the open-source machine learning framework PyTorch suffered a supply chain attack. Attackers uploaded a malicious version of the ‘torchtriton’ dependency to the Python Package Index (PyPI). When users installed nightly builds of PyTorch, the malicious package exfiltrated sensitive data from their systems. The PyTorch team responded by removing the compromised dependency and advising users to uninstall the affected versions. Read More: PyTorch dependency ‘torchtriton’ on PyPI Supply Chain Attack
3. 3CX Supply Chain Attack (2023)
In March 2023, the 3CX Desktop App, a widely used application for voice and video communications, was compromised in a sophisticated supply chain attack. The attackers infiltrated the app’s software build environment, embedding malicious code into the application. This resulted in the distribution of trojanized versions to users through the official update channels, potentially impacting a significant number of organizations globally. Read More: 3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible
4. Okta Support System Breach (2023):
In October 2023, identity and authentication service provider Okta reported a significant supply chain breach involving its customer support system. The attack began when threat actors compromised an Okta employee’s personal Google account accessed via a work laptop. This led to the deployment of malware, allowing attackers to infiltrate Okta’s customer support system.Through this breach, attackers accessed and exploited unsanitized HTTP Archive (HAR) files uploaded by customers in support cases. These files contained sensitive data, including session tokens, which the attackers used to attempt unauthorized access to the internal systems of Okta’s customers, such as 1Password, BeyondTrust, and Cloudflare. While most companies detected and ejected the attackers before any major damage occurred, the incident underscored the vulnerabilities associated with third-party service providers in the supply chain. Read More: Understanding the Okta supply chain attack of 2023: A comprehensive analysis
Key Takeaways
Modern cloud-centric supply chain attacks differ significantly from traditional supply chain attacks, which primarily targeted physical goods, logistics, and manufacturing processes through counterfeiting, tampering, or theft. Today’s attacks focus on exploiting the digital dependencies of cloud environments, including third-party APIs, software repositories, and cloud-native development pipelines. These attacks, such as the SolarWinds and 3CX breaches, leverage the interconnected nature of cloud ecosystems to infiltrate multiple organizations through a single compromise.
This shift highlights the urgent need for both Cloud Service Providers (CSPs) and Cloud Service Customers (CSCs) to adopt the shared responsibility model. Through the implementation of robust security measures such as advanced threat detection, comprehensive identity management, and regular security audits, both parties can collaboratively mitigate the risks posed by this growing threat.
Closing Remarks
Supply chain attacks are an evolving threat with far-reaching implications for organizations that rely on cloud services. Organizations that utilize third-party vendors and cloud providers without conducting thorough verification and due diligence risk exposing vulnerabilities that attackers can exploit to compromise critical systems. This risk was clearly demonstrated in high-profile breaches such as SolarWinds and 3CX, where attackers leveraged supply chain weaknesses to infiltrate multiple organizations.
In Part 2, we will explore how the three major CSPs (AWS, Microsoft Azure, and Google Cloud) are addressing these risks and what measures they are implementing to secure their ecosystems against supply chain attacks.
Further Reading
- Securing Open Source: Lessons from the Software Supply Chain Revolution
- The 3 types of cyberattacks affecting global supply chains
- The Kaseya Attack: Everything to Know – What 20 years of supply chain attacks looks lik
- Dependency Confusion: How I Hacked Into Apple, Microsoft and Dozens of Other Companies
- National Cyber Security Centre – Supply chain security guidance
- Top 15 software supply chain attacks: Case studies
Reference
- A Brief History of Supply Chain Attacks
- Software Supply Chain Attacks: Insights and Defense Strategies
- Throwback Attack: RSA SecurID attack shows the importance of protecting critical assets
- Dependency Confusion Attacks and Prevention: Register Your Private Package Names
- API abuse in the cloud
- AWS Impersonated in Credential Phishing Attack [Abnormal Security] ****
- The Kaseya Attack: Everything to Know
- Supply chain attacks show why you should be wary of third-party providers
![AWS Impersonated in Credential Phishing Attack [Abnormal Security]](https://irradiated-water-407.notion.site/image/attachment%3A2bb77abe-a892-47b8-b6be-5b7f066805fe%3Aimage.png?table=block&id=18917b9e-4a8c-8083-8da0-e7c6bc9fc5d7&spaceId=b6d6aff8-253a-4d6d-82e6-782375602db3&width=1360&userId=&cache=v2)
