Understanding Supply Chain Attacks in the Cloud: An Introduction to the Silent Threat
In March 2024, Microsoft employee and PostgreSQL developer Andres Freund while investigating a performance regression in Debian Sid he noticed unusually high CPU usage in SSH connections and errors in the Valgrind memory debugging tool. During his investigation, Freund discovered a backdoor in the popular Xz Utils application. He reported the findings to the Openwall Project’s security mailing list, alerting software vendors.
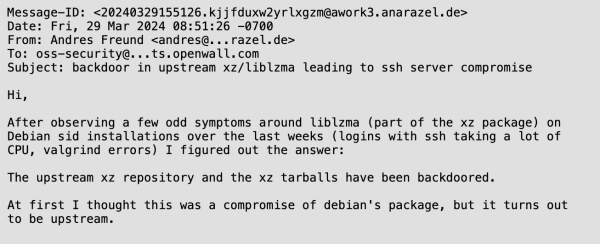 Andrew’s first report to Openwall mailing list
Andrew’s first report to Openwall mailing list
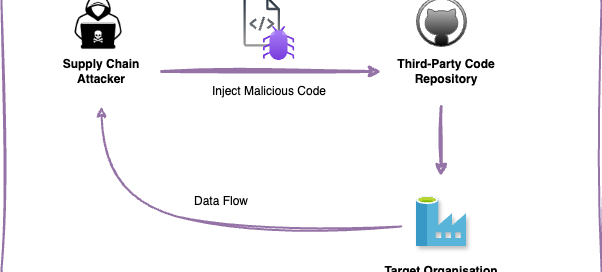
The Xz Utils backdoor supply chain attack involved the insertion of malicious code into a widely used open-source library, Xz Libs, which is essential for Unix-based systems. The attacker had attempted to obfuscate the backdoor by implementing it in multiple stages. This supply chain attack gave attackers unauthorized access and control over systems using the compromised versions of the library.
The threat was particularly severe, as it targeted a critical part of server infrastructure used by millions. This incident highlighted once more the raising trend in sophisticated supply chain attack over the recent years.
Introduction to Supply Chain Attacks
What Are Supply Chain Attacks?
Supply chain attacks have existed for decades, initially focusing on physical goods and manufacturing processes, often referred to as physical supply chain attacks. Historically, adversaries exploited networks of