Breaking The Chain: How Threat Actors Exploit Supply Chains in Major CSPs
Introduction
In 2022, a significant phishing campaign known as “0ktapus” targeted Okta users, successfully bypassing their one-time code-based multi-factor authentication (MFA). Attackers sent SMS messages containing links to phishing sites that closely resembled the victims’ organizational Okta login pages. Unsuspecting employees entered their corporate credentials and 2FA codes into these fraudulent sites, which were then captured by the attackers. Many enterprises that integrated Okta with cloud service providers such as AWS, Azure, and Google Cloud Platform (GCP) for authentication and security were affected. The complexity of cloud-native architectures, shared responsibility models, and the dynamic nature of cloud environments further amplify these challenges.

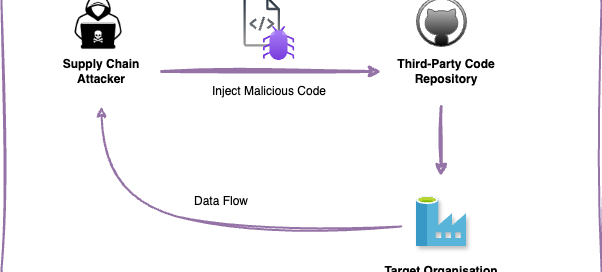
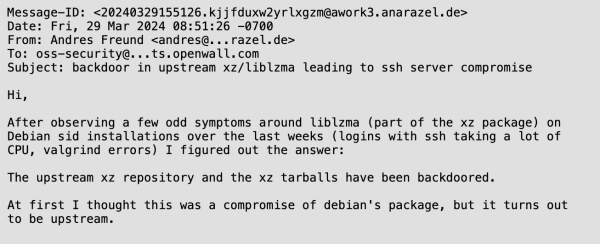
Cloud supply chain attacks are becoming increasingly frequent and sophisticated, posing significant risks to organizations. As businesses rely more on cloud services for digital transformation, securing cloud supply chains has become a critical challenge. Unlike traditional IT environments, cloud supply chains involve multiple interconnected vendors, third-party software providers, and dependencies, each introducing security vulnerabilities. A single compromised component, such as a vulnerable third-party API, misconfigured software update, or exploited identity federation, can serve as an entry point for widespread breaches, leading to data theft, service disruptions, and regulatory